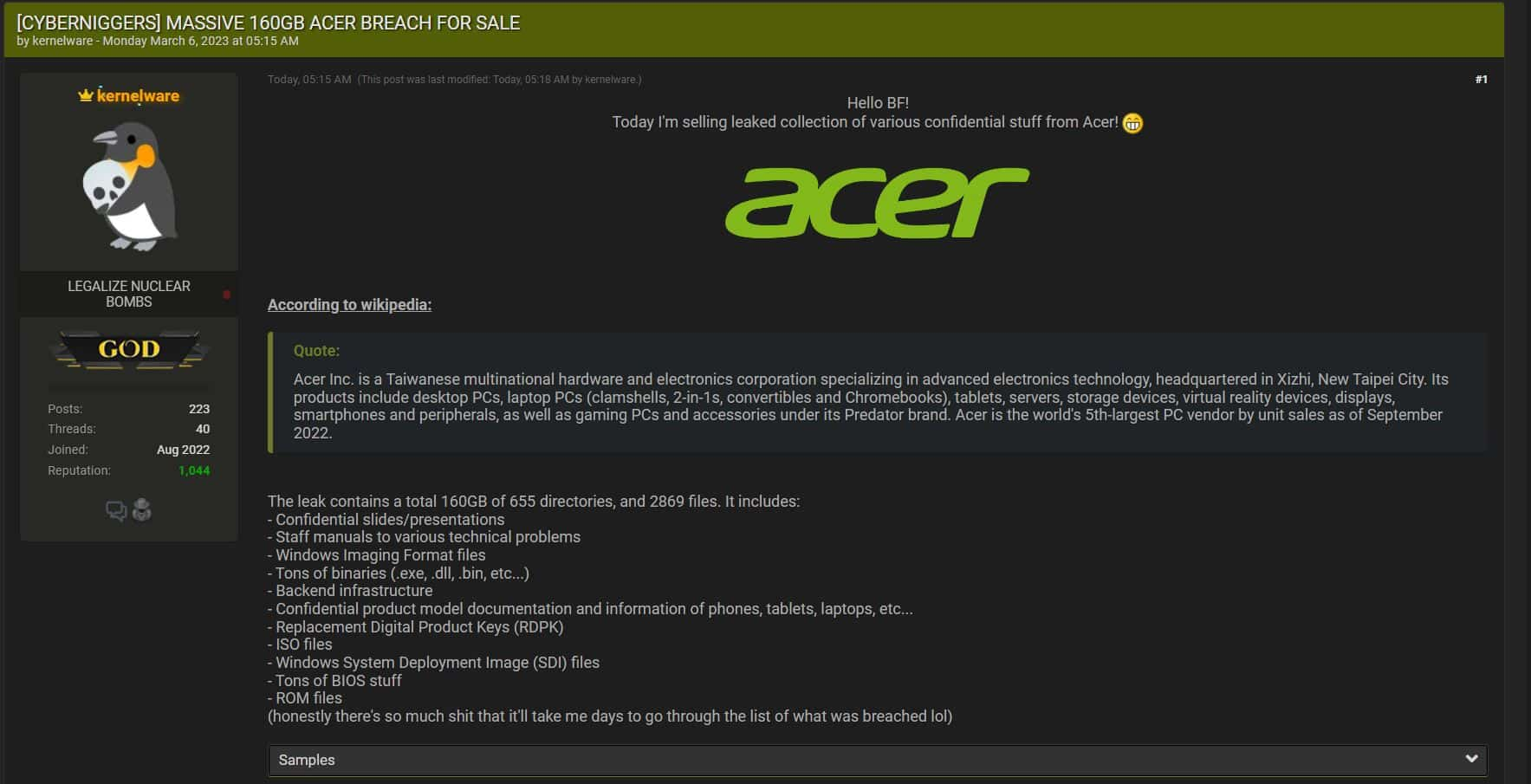
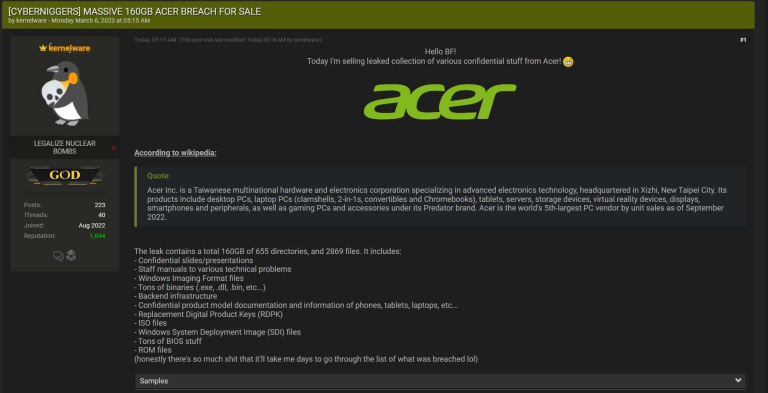
The recent Acer data breach has sent shockwaves through the cybersecurity community after the hacking group Pakistan Cyber Army claimed responsibility for infiltrating an Acer server located in Europe. They allegedly extracted personal data for approximately 40,000 individuals, including sensitive information such as names, email addresses, and phone numbers. Furthermore, the attack reportedly included the theft of several pieces of source code, amplifying concerns over Acer’s cybersecurity practices. This incident comes at a precarious time for Acer, as the company is already grappling with financial issues that have recently affected its stock market performance. As this story unfolds, it highlights not only the vulnerabilities facing large corporations like Acer but also the ever-evolving landscape of cybersecurity threats in today’s digital age.
In a startling revelation, a significant security incident involving Acer has emerged, characterized by claims from the hacking collective known as Pakistan Cyber Army regarding unauthorized access to company systems. The attack is said to have resulted in the theft of confidential personal information belonging to thousands of users, raising alarms about personal data safety in the tech industry. Additionally, the breach coincides with Acer facing scrutiny over its financial accountability, a situation now complicated by questions surrounding the integrity of their cybersecurity measures. This scenario draws attention to broader concerns about the impact of cybercriminal activities on major corporations. As a noteworthy chapter in ongoing cybersecurity news, the Acer incident serves as a crucial reminder of the intersection between technology vulnerabilities and financial accountability.
Understanding the Acer Data Breach Incident
The Acer data breach incident has raised significant concerns about cybersecurity practices in major corporations. The hacking group known as the Pakistan Cyber Army has boldly claimed responsibility for breaching Acer’s server in Europe and stealing sensitive personal information. Reports indicate that this breach involves the data of approximately 40,000 individuals, sparking fears of widespread identity theft and privacy violations. In an age where personal data is a valuable commodity, such an incident underscores the vulnerabilities faced by even prominent companies in the tech industry.
Acer, recognized as the second-largest laptop manufacturer globally, now finds itself at a crucial juncture, needing to address both the ramifications of this data leak and the public’s trust. With screenshots of compromised information such as names, email addresses, and phone numbers circulating online, the company is under immense pressure to reassure its customers and stakeholders. It remains to be seen how Acer’s management will navigate through this storm, especially with another layer of complexity due to its ongoing financial issues.
The Role of the Pakistan Cyber Army
The Pakistan Cyber Army’s claim of responsibility for the Acer server hack highlights the growing trend of hacktivism, where groups take matters into their own hands to expose weaknesses within large corporations. This incident adds to a troubling series of breaches reported by various organizations over the past few weeks, indicating a coordinated effort to target companies with significant data repositories. Understanding the motives behind such hacks is crucial for both cybersecurity professionals and businesses striving to enhance their defenses against similar threats.
Additionally, this claim puts the spotlight on the tactical capabilities of the Pakistan Cyber Army, which, in the current cybersecurity landscape, could potentially draw inspiration from previous high-profile attacks. Such groups often leverage social media and other communication platforms to announce their operations and to instill fear among major corporations. As a response, businesses must implement robust security measures, educate employees about the importance of cybersecurity, and stay informed about evolving threats to mitigate risks effectively.
Impact on Acer’s Financial Stability
In the wake of the Acer data breach, concerns about the company’s financial stability have come to the forefront. Once again facing scrutiny, Acer’s financial integrity is at stake, especially after reports of irregularities in its inventory and accounts receivable. Just days before the breach, Acer shares experienced a plummet on the Taiwan stock exchange, with a staggering $150 million write-off as a result of an audit revealing financial discrepancies. These challenges, compounded by the data breach announcement, could lead to long-lasting trust issues among investors and consumers.
Moreover, the interconnection between the Acer server hack and the company’s financial problems raises questions. Analysts and stakeholders are left wondering whether this cyber attack was opportunistic or strategically timed to exploit Acer’s vulnerabilities during a period of instability. It is critical for Acer to not only address the cybersecurity challenges posed by the breach but also to reassure its investors about future fiscal health and governance standards.
Acer’s Corporate Response and Accountability
Acer’s corporate response to the hacking allegations, as articulated by media relations director Lisa Emard, indicates a proactive approach toward addressing the cyber threat. The company’s efforts to liaise with its European officials to verify the breach demonstrate an awareness of the gravity of the situation. Transparent communication with the public and affected individuals will be vital for restoring trust after such a damaging incident. Additionally, establishing a clear action plan to enhance cybersecurity measures will be essential in mitigating the impact of this breach.
Accountability also extends to Acer’s leadership, as evidenced by the statement from CEO J.T. Wang vowing to relinquish remuneration amidst financial challenges. As the company navigates through accusations of irregular financial practices, it becomes imperative that Acer not only tackles the immediate fallout from the data breach but also reassures stakeholders of its commitment to ethical and transparent business practices moving forward.
Strategies for Enhancing Cybersecurity in Major Corporations
In light of the recent Acer incident, there is a pressing need for major corporations to reassess and enhance their cybersecurity strategies. With cyber threats becoming increasingly sophisticated, companies must adopt a multi-faceted approach, including regular risk assessments, employee training programs, and the implementation of advanced encryption technologies to protect sensitive data. Furthermore, establishing incident response plans can prepare organizations to act swiftly and effectively in the event of a breach.
Moreover, collaboration with cybersecurity firms and continuous monitoring of potential vulnerabilities is essential. As evidenced by the importance placed on cybersecurity in the Acer breach, sustained vigilance is vital for reducing the risk of personal data theft. Large organizations must prioritize cybersecurity measures not merely as compliance requirements, but as integral parts of their operational strategies, fostering an overall culture of security awareness.
The Broader Context of Cybersecurity Challenges
The Acer data breach is a stark reminder of the broader cybersecurity challenges facing many companies today. While Acer finds itself in the spotlight, it is essential to recognize that other significant entities, such as Lockheed Martin, L-3 Communications, and Sony, have also experienced breaches recently. This surge in cyber incidents indicates a pattern that businesses must acknowledge and address, for they can no longer assume that their systems are impervious to attacks.
Moreover, the implications of these breaches extend beyond immediate data loss, affecting consumer trust and overall brand reputation. As more organizations fall victim to hacking attempts, there is a growing urgency for a collective industry response. Cybersecurity regulations, standards, and best practices should evolve to reflect the current threat landscape, aiding companies like Acer in fortifying their defenses against imminent threats.
Legal Implications of Data Breaches
The legal implications stemming from the Acer data breach could be substantial, particularly with stringent data protection laws now in effect across various jurisdictions. Companies that fail to adequately protect consumer data not only face the risk of lawsuits but also may incur hefty fines from regulatory bodies. As Acer works to navigate through the aftermath of its data breach, it must prepare for potential legal actions by affected individuals as well as scrutiny from data protection authorities.
Furthermore, consumer right to privacy is becoming increasingly emphasized in today’s digital landscape. Organizations like Acer need to be diligent in their compliance with laws such as the General Data Protection Regulation (GDPR) in Europe, which mandates strict protocols concerning the handling of personal data. The impact of non-compliance can be detrimental, both financially and reputationally, making legal foresight a critical component of any corporate cybersecurity strategy.
Preventing Future Data Breaches
In the aftermath of the recent data breach, it is critical for Acer and similar corporations to focus on preventing future incidents. Developing a comprehensive cybersecurity framework that includes regular updates to software, firewalls, and anti-virus protection is foundational. Additionally, employing ethical hacking strategies to uncover vulnerabilities within their systems can empower companies to address weaknesses before they can be exploited by malicious actors.
Investing in continuous education and training for employees is also essential to prevent data breaches. Instilling a culture of cybersecurity awareness can significantly reduce the likelihood of human error, a common trigger for breaches. With ongoing threats from groups like the Pakistan Cyber Army, organizations must adopt a proactive stance and remain vigilant, utilizing all available resources to enhance their cyber defenses.
The Importance of Cyber Insurance
In light of data breaches like the one involving Acer, the importance of cyber insurance cannot be understated. Cyber insurance policies can provide essential financial protection to companies facing the repercussions of data breaches, covering costs related to legal fees, customer notification, and recovery efforts. For corporations navigating an uncertain cyber landscape, having adequate cyber insurance can offer peace of mind and a safety net against financial fallout.
As part of a broader risk management strategy, businesses must carefully evaluate their cyber insurance options to ensure comprehensive coverage. This includes understanding policy specifics, such as coverage limits and exclusions, to make informed decisions when selecting a provider. By integrating cyber insurance into their overall risk posture, organizations can better prepare for and respond to the financial implications of data breaches.
Frequently Asked Questions
What happened during the Acer data breach involving the Pakistan Cyber Army?
The Acer data breach occurred when the hacking group Pakistan Cyber Army successfully compromised an Acer server in Europe, claiming to have stolen personal data of approximately 40,000 individuals. The hackers alleged that they also accessed sensitive source code stored on the server.
What type of personal data was stolen in the Acer data breach?
The personal data theft during the Acer data breach included names, email addresses, phone numbers, and additional information of 40,000 individuals, as reported by The Hacker News.
How has Acer responded to the claims regarding the data breach?
Acer’s media relations director, Lisa Emard, stated that the company’s U.S. operations have no information about the Acer data breach and are currently seeking a response from officials in Europe regarding the claims made by the Pakistan Cyber Army.
Is the Acer data breach connected to the company’s financial issues?
It remains unclear whether the Acer data breach is linked to its recent financial difficulties, which include an audit revealing irregularities that led to a significant stock price drop and a $150 million write-off.
What cybersecurity news highlights similar breaches to the Acer data breach?
The Acer data breach is among several major cybersecurity incidents, with other companies such as Lockheed Martin, L-3 Communications, and Sony experiencing similar breaches just prior to this event.
What measures should individuals take following the Acer data breach?
In light of the Acer data breach, individuals should monitor their personal accounts for any unusual activity, change passwords, and consider placing fraud alerts on their credit reports to protect against identity theft.
Where can I find more information about the Acer data breach?
For comprehensive updates and analysis on the Acer data breach, you can visit cybersecurity news platforms like The Hacker News, along with Computerworld’s Security Topic Center, which covers similar data security issues.
| Key Point | Details |
|---|---|
| Breach Announcement | Pakistan Cyber Army claimed to have breached an Acer server and stolen data of around 40,000 individuals. |
| Stolen Data | The stolen data includes names, email addresses, phone numbers, and source code. |
| Company Response | Acer’s U.S. operations director stated that they have no information regarding the breach and that European officials are being contacted. |
| Financial Context | Acer’s stock fell following an audit revealing financial irregularities leading to a $150 million write-off. |
| Leadership Accountability | Chairman J.T. Wang stated he would forfeit his salary and bonus to take responsibility for the financial charge. |
| Other Compromised Companies | Acer joins a list of recent breaches affecting companies like Lockheed Martin, L-3 Communications, and Sony. |
Summary
The Acer data breach has raised significant concerns as hackers, identified as the Pakistan Cyber Army, compromised sensitive information belonging to approximately 40,000 individuals. This incident not only highlights the vulnerabilities present within major companies like Acer but also coincides with scrutiny on the company’s financial practices. As Acer seeks to clarify the breach’s specifics and manage its financial woes, the implications of this attack could impact its reputation and trust among consumers. Moving forward, it’s crucial for Acer to enhance its security measures to prevent future breaches and safeguard personal data.