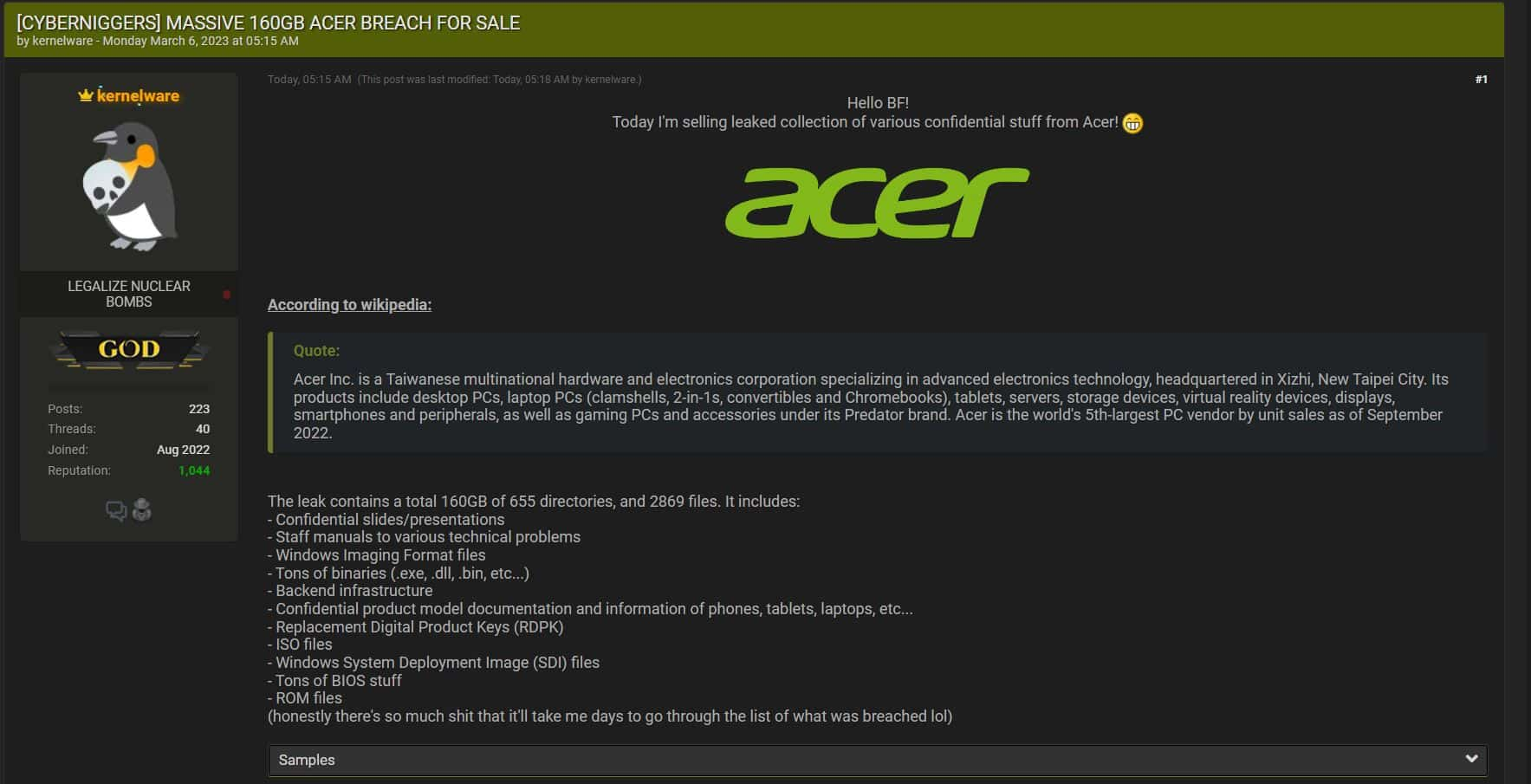
The recent Acer data breach has raised significant concerns about cybersecurity, with reports surfacing that the Packard Bell division in Europe was targeted in a malicious hacker attack. According to Acer’s statement, sensitive personal data belonging to approximately 40,000 customers was compromised, including names, addresses, phone numbers, and email addresses. Thankfully, no credit card information was exposed during this cyber incident. The notorious hacking group, Pakistan Cyber Army, has claimed responsibility for this alarming data theft, which has prompted Acer to launch a thorough investigation into the matter. As the digital landscape grows increasingly perilous, this breach serves as a stark reminder of the importance of robust cybersecurity measures to protect personal information from falling into the wrong hands.
The recent infiltration experienced by the Taiwanese tech company Acer, known for its computers and peripherals, unveils a significant breach of consumer trust and data security. The assault, attributed to the hackers identifying themselves as the Pakistan Cyber Army, has exposed sensitive information from customers associated with the Packard Bell brand. This incident underscores the ongoing threat of personal data theft and highlights the vulnerabilities present within many tech infrastructures. Such cybersecurity lapses not only compromise individual safety but also tarnish a brand’s reputation, showcasing the urgent need for enhanced protective protocols. As companies strive to safeguard against these sophisticated cyber threats, each breach serves as a crucial lesson in reinforcing digital defenses.
Understanding the Acer Data Breach
The Acer data breach has emerged as a significant cybersecurity incident, raising concerns about the safety of personal information in the digital age. Reports indicate that this breach primarily affected Acer’s Packard Bell division, revealing vulnerabilities in how user data is protected. As personal data theft continues to be a prevalent threat, this incident serves as a stark reminder for both consumers and corporations alike to enhance their cybersecurity measures.
During the ongoing investigation into the Acer hacker attack, it has become evident that sensitive customer details, including names, addresses, and email accounts, were compromised. While Acer has confirmed that no financial information was included in this breach, the exposure of personal data can lead to various risks, such as identity theft and phishing scams. The incident underlines the importance of robust data protection protocols in safeguarding user information from cybercriminals.
The Impact of the Packard Bell Data Leak
The recent Packard Bell data leak associated with Acer not only affects individual customers but also has broader implications for the entire industry. Such cyber breaches can lead to a decline in consumer trust, which is vital for companies that rely heavily on customer loyalty. As more information becomes available about the scale and nature of the attack, companies will need to reassess their cybersecurity strategies to prevent similar occurrences.
Moreover, the fallout from the Packard Bell data leak could have a ripple effect on various stakeholders, including partners and third-party vendors. Companies must work collaboratively to ensure that their data protection standards are high, reducing the likelihood of being targeted by hackers. The financial implications of such breaches could also be substantial, not to mention the potential for legal repercussions if customer data protection regulations were violated.
Pakistan Cyber Army’s Role in the Cybersecurity Breach
The involvement of the Pakistan Cyber Army in the Acer hacker attack highlights the growing threat posed by organized cybercriminal groups. Their claim of accessing the personal data of approximately 40,000 individuals stands as a testimony to the capabilities of these hackers. These groups often leverage sophisticated methods to infiltrate systems, making it imperative for companies to fortify their defenses against such attacks.
Additionally, the Pakistan Cyber Army’s actions are often politically motivated, aiming to retaliate against perceived injustices. The defacement of India’s Central Bureau of Investigation website is a prime example of how cyber warfare is being waged in the digital realm. Understanding the motivations behind these attacks can help organizations better prepare for potential threats and develop comprehensive incident response strategies.
The Importance of Cybersecurity Vigilance
As the Acer data breach illustrates, maintaining cybersecurity vigilance is crucial for protecting sensitive customer information. Organizations must prioritize regular audits of their data security measures, implement strong encryption protocols, and provide ongoing training for staff about potential threats. Being proactive in cybersecurity can significantly reduce the risk of data theft during hacking incidents.
Furthermore, having a robust incident response plan in place allows companies to react swiftly and decisively when a breach occurs. This can minimize damage, protect assets, and reassure customers that their data is being handled responsibly. For Acer, enhancing their cybersecurity framework post-breach will be an essential step in restoring consumer trust and ensuring that similar incidents do not reoccur.
Customer Awareness and Data Protection
In light of the recent breaches involving major companies like Acer, it’s essential for customers to be aware of how their data is being handled. Users must understand the importance of safeguarding their personal information and the potential risks associated with sharing sensitive data online. This awareness is a critical component of fostering a safer digital environment.
Additionally, customers should take it upon themselves to utilize best practices for data protection. This includes using strong, unique passwords for different accounts, enabling two-factor authentication, and being vigilant about unsolicited communication that may lead to phishing attempts. Empowering customers with the knowledge of how to protect themselves can significantly mitigate the impact of any data breaches.
Analyzing the Response of Acer to the Breach
Acer’s response to the hacker attack has been scrutinized as stakeholders await more comprehensive communication regarding the breach. Transparency in addressing such incidents is crucial for rebuilding trust with customers. By providing timely updates and clarifying what data was affected, Acer can demonstrate accountability and reinforce its commitment to data security.
Moreover, Acer’s post-breach strategy may involve engaging cybersecurity experts to ensure that vulnerabilities are addressed immediately and to prevent future incidents. This proactive approach not only protects customer data but also enhances the overall security infrastructure of the company, setting a precedent for industry best practices.
Implications for Data Privacy Laws
The Acer data breach also raises significant questions regarding data privacy laws and regulations that govern how organizations manage customer information. As incidents like this become more commonplace, there will likely be calls for stricter regulations to ensure that companies adequately protect sensitive data from unauthorized access.
Regulatory bodies may consider implementing more stringent measures that require regular security assessments and mandatory reporting of data breaches. Companies found neglecting their duties in data protection may face hefty fines and reputational damage. For organizations, this emphasizes the need for compliance in addition to adopting best cybersecurity practices to avoid the repercussions of data breaches.
Preventing Future Hacking Incidents
Preventing future hacking incidents involves continuous improvement in cybersecurity practices. Companies like Acer must invest in advanced technology and threat intelligence services that provide real-time monitoring and proactive threat detection. This innovative approach allows for quicker identification and mitigation of potential attacks before they can escalate.
Additionally, fostering a culture of cybersecurity within organizations reinforces important practices. Regular training sessions, simulations of cyber incidents, and encouraging employees to report suspicious activity contribute to a well-prepared workforce that can significantly reduce the likelihood of data breaches occurring in the first place.
Exploring Cybersecurity Trends in the Industry
The Acer hacker attack is part of a larger troubling trend in the cybersecurity landscape, where high-profile breaches are becoming increasingly commonplace. Organizations across various sectors must understand that as technology evolves, so do the tactics employed by cybercriminals. Staying informed about emerging cybersecurity trends is essential for developing effective defenses.
The rise of ransomware attacks, phishing schemes, and data leaks have necessitated a shift in how businesses approach data security. Companies are now looking into multi-layered security strategies that not only protect their data but also enhance employee training and incident response plans. Understanding these trends allows organizations to adapt and protect themselves from the evolving cyber threat landscape.
Frequently Asked Questions
What happened during the Acer data breach?
The Acer data breach involved a cybersecurity attack that compromised customer data from its Packard Bell division in Europe, leading to the theft of names, addresses, phone numbers, emails, and system serial numbers. However, Acer confirmed that credit card information was not affected.
Who is responsible for the Acer hacker attack?
The hacker group known as Pakistan Cyber Army has claimed responsibility for the Acer hacker attack. They asserted that they obtained personal data from Acer’s server, impacting approximately 40,000 individuals.
What type of personal data was stolen in the Acer data breach?
In the Acer data breach, the stolen personal data included customer names, addresses, phone numbers, emails, and system serial numbers, but there was no theft of credit card information.
How is Acer responding to the cybersecurity breach?
Acer is currently investigating the cybersecurity breach and is working to understand the full extent of the attack. They have stated that they are taking the matter seriously and will keep customers informed about any developments.
Was any financial information compromised in the Packard Bell data leak?
No, during the Packard Bell data leak related to the Acer data breach, the company confirmed that no credit card or financial information was compromised.
What are the implications of the Acer data breach for affected customers?
Affected customers may be at risk of identity theft or phishing attacks due to the exposure of their personal data from the Acer data breach. It is recommended that they remain vigilant and monitor their accounts closely.
What can customers do to protect themselves after the Acer hacker attack?
In light of the Acer hacker attack, customers should consider changing their passwords, enabling two-factor authentication where possible, and being cautious of suspicious communications that may exploit the data stolen during the breach.
Has the Pakistan Cyber Army released any further information about the Acer breach?
As of now, the Pakistan Cyber Army has not released any further information regarding the Acer data breach despite their initial claims of responsibility and intentions to explain their motives.
How significant is the Acer data breach in terms of cybersecurity threats?
The Acer data breach is a significant incident, highlighting ongoing cybersecurity threats faced by major companies. It underscores the need for strong data protection measures and awareness of potential targeted attacks by hacker groups like the Pakistan Cyber Army.
What steps should organizations take to prevent incidents like the Acer cybersecurity breach?
Organizations should implement robust cybersecurity measures such as regular security audits, employee training on data protection, and incident response plans to prevent breaches like the Acer cybersecurity breach.
| Key Point | Details |
|---|---|
| Acer Data Breach | Acer is investigating a breach that exposed customer data. |
| Affected Division | The attack involved Acer’s Packard Bell division in Europe. |
| Data Compromised | Customer names, addresses, phone numbers, emails, and system serial numbers were stolen. |
| Credit Card Security | No credit card information was compromised during this breach. |
| Hacker Group Involved | Pakistan Cyber Army claims to have obtained data of approximately 40,000 individuals. |
| Current Status | The investigation is ongoing; Acer has not provided additional details. |
| Motivation Behind Attack | The hackers claim their actions were retaliation for Indian attacks on Pakistani websites. |
| Previous Incidents | The same hacker group previously defaced the Indian Central Bureau of Investigation’s website. |
Summary
The Acer data breach has raised significant concerns regarding customer data security following a hacker attack that compromised sensitive information from its Packard Bell division. The breach impacted approximately 40,000 individuals, exposing personal details such as names, addresses, and emails, although credit card information remained safe. The breach illustrates the ongoing threats faced by corporations in securing customer data against determined hacking groups like the Pakistan Cyber Army, which has claimed responsibility amid allegations of cyber warfare. As investigations continue, it is crucial for Acer and similar organizations to bolster their cybersecurity measures to protect against future threats.